Increased use of ICT has led to changing patterns of employment due to the increased use of ICT
I partially agree with the statement because teleworking has now became an important part of employment for many companies and profesions such as jounalism. Teleworking allows for people to work from home exactly the same way they would work in an office, teleworking can benifit both the worker and the company as it saves the worker money on transport to work and allows them to be more creative in an area they feel comfortable in. However some workers may not be as productive without any supervision and may get easily distracted in their home so will be less productive. This shows that ICT has changed the way people can be employed and the role they can play in the company as ICT allows for more flexibility in both hours worked and the type of job a worker can do.
In addition ICT has improved workforce skills as when a new ICT system is implemented into the workplace to replace an out dated system the staff must be trained in how to correctly use the system so that the ICT system is benificial for them, and does not hinder their performance. Furthermore if a company already has an ICT system then before hiring someone they will make sure that the worker will have the correct qualification, therefore this will encourage more people to achieve qualifications in an effort to improve there skills with ICT which will allow them to excel at work.
Employers can now monitor the workforce using their ICT system this can be a great benifit to the company as they can keep this a secret and find out which workers are not being productive with the use of computers, this then enables the company to disiplin them of find another employe. On the other hand if the company informs the workers of the capability to monitor the work done, this may encourage the workers to be more productive as they feel feel pressured into working as they know they could be being watched, also it will limit the use of personal internet use which can be a major problem.
In conclusion ICT had led to many changes in emplyment and in the workforce as ICT enables simple tasks to be carried out more efficiently and also allows a lot of flexibility in the workplace as ICT allows workers to work for home and share documents with other workers on the ICT system. Finally ICT has changed the patterns of emplyment due to skills being needed to operate the system and the ability to work from home which means you do not need to look local when hiring someone.
ICT and Internet Laws
Sunday, 29 April 2012
Thursday, 26 April 2012
Operating Systems
Why do you think that Operarting Systems are necessary in order for a computer to run effectively?
MULTI-USER:This allows one or more user to log into a system. Thus the operating system must contain a user account database, which contains user name, default home directory, user passwords and user right.
MULTIPROCESSING:This allows two or more processes to be used at a time. Here the operating system must decide if it can run the different processes on individual processors. It must also manage the common memory between processors
MEMORY MANAGEMENT:This involves allocating, and often to create a virtual memory for program. Paging which means organizing data so that the program data is loaded into pages of memory. Another method of managing memory is swapping. This involves swapping the content of memory to disk storage.
MULTI-THREADING:Processes are often split into smaller task, named threads. This thread allows smoother operations
Backup utilities can make a copy of all information stored on a disk, and restore either the entire disk (e.g. in an event of disk failure) or selected files (e.g. in an event of accidental deletion).
Data compression utilities output a shorter stream or a smaller file when provided with a stream or file.
Disk checkers can scan operating hard drive.
The OS (Operating System) ensures that all the software has access to the different resources it need to run successfully and controls the running and scheduling of all these processes and manages the share of the Central Processing Unit's processing time that is used by the different processes, making the computer run effictively.
Explain four tasks performed by an Operating System?
Functions Of Operating System
Today most operating systems perform the following important functions:
1. Processor management, that is, assignment of processor to different tasks being performed by the computer system.
2. Memory management, that is, allocation of main memory and other storage areas to the system programmes as well as user programmes and data.
3. Input/output management, that is, co-ordination and assignment of the different output and input device while one or more programmes are being executed.
4. File management, that is, the storage of file of various storage devices to another. It also allows all files to be easily changed and modified through the use of text editors or some other files manipulation routines.
5. Establishment and enforcement of a priority system. That is, it determines and maintains the order in which jobs are to be executed in the computer system.
6. Automatic transition from job to job as directed by special control statements.
7. Interpretation of commands and instructions.
8. Coordination and assignment of compilers, assemblers, utility programs, and other software to the various user of the computer system.
9. Facilities easy communication between the computer system and the computer operator (human). It also establishes data security and integrity
Today most operating systems perform the following important functions:
1. Processor management, that is, assignment of processor to different tasks being performed by the computer system.
2. Memory management, that is, allocation of main memory and other storage areas to the system programmes as well as user programmes and data.
3. Input/output management, that is, co-ordination and assignment of the different output and input device while one or more programmes are being executed.
4. File management, that is, the storage of file of various storage devices to another. It also allows all files to be easily changed and modified through the use of text editors or some other files manipulation routines.
5. Establishment and enforcement of a priority system. That is, it determines and maintains the order in which jobs are to be executed in the computer system.
6. Automatic transition from job to job as directed by special control statements.
7. Interpretation of commands and instructions.
8. Coordination and assignment of compilers, assemblers, utility programs, and other software to the various user of the computer system.
9. Facilities easy communication between the computer system and the computer operator (human). It also establishes data security and integrity
There are many different brands of Operating System. Identify four of the most common ones.
Linux
Windows
Lion
IOS
Explain how an Operating System can manage numerous people working at the same time. What is this called?
An operating system can manage numerous people working on at the same time becasue of the following features.
MULTI-USER:This allows one or more user to log into a system. Thus the operating system must contain a user account database, which contains user name, default home directory, user passwords and user right.
MULTIPROCESSING:This allows two or more processes to be used at a time. Here the operating system must decide if it can run the different processes on individual processors. It must also manage the common memory between processors
MEMORY MANAGEMENT:This involves allocating, and often to create a virtual memory for program. Paging which means organizing data so that the program data is loaded into pages of memory. Another method of managing memory is swapping. This involves swapping the content of memory to disk storage.
MULTI-THREADING:Processes are often split into smaller task, named threads. This thread allows smoother operations
Utility programs provide a "toolbox" of common tasks which help the computer to run more effeciently. Identify and explain three utilities that are available.
Anti-virus utilities scan for computer viruses.
Explain the difference between the three different methods of processing and provide and example of each
Batch Processing
•This is a method where the information to be organized is sorted into groups to allow for efficient and sequential processing.
Online Processing
•This is a method that utilizes Internet connections and equipment directly attached to a computer. It is used mainly for information recording and research.
Real-Time Processing
•This technique has the ability to respond almost immediately to various signals in order to acquire and process information.
Distributed Processing
•This method is commonly utilized by remote workstations connected to one big central workstation or server. ATMs are good examples of this data processing method.
For each of the following tasks that can be performed on a computer, state whether they would be a job for the operating system or an application;
Controlling the engine management for a car Application
Writing a letter Application
Backing up the system Operating System
Calculating company accounts Application
Allocating memory to allow programs to run Operating System
Writing a report Application
Communication with a partner Application
Batch Processing
•This is a method where the information to be organized is sorted into groups to allow for efficient and sequential processing.
Online Processing
•This is a method that utilizes Internet connections and equipment directly attached to a computer. It is used mainly for information recording and research.
Real-Time Processing
•This technique has the ability to respond almost immediately to various signals in order to acquire and process information.
Distributed Processing
•This method is commonly utilized by remote workstations connected to one big central workstation or server. ATMs are good examples of this data processing method.
For each of the following tasks that can be performed on a computer, state whether they would be a job for the operating system or an application;
Controlling the engine management for a car Application
Writing a letter Application
Backing up the system Operating System
Calculating company accounts Application
Allocating memory to allow programs to run Operating System
Writing a report Application
Communication with a partner Application
Wednesday, 18 April 2012
User Interfaces
Explain what "user interface" means.
An interface is a set of commands or menus through which a user communicates with a program. A command-driven interface is one in which you enter commands. A menu-driven interface is one in which you select command choices from various menus displayed on the screen.
The user interface is one of the most important parts of any program because it determines how easily you can make the program do what you want. A powerful program with a poorly designed user interface has little value. Graphical user interfaces (GUIs) that use windows, icons, and pop-up menus have become standard on personal computers. What are the three main types of user interface called?
Graphical user interface
is sometimes shortened to GUI. The user chooses an option usually by pointing a mouse at an icon representing that option
Menu driven interfaces
The user is offered a simple menu from which to choose an option. One menu often leads to a further menu. Part of the screen may have an instruction followed by a numbered list of options to choose from.Command-line interfaces
A command-line interface allows the user to interact with the computer by typing in commands. The computer displays a prompt, the user keys in the command and presses enter or return.Explain what you need to do to use a command line driven U.I
To get to the command line on your computer click on the Start button, click on Run, then type "cmd" in the run box. You will go to a black box called DOS. You will also see the command line prompt C:>, this is where you type in DOS commands. You can use DOS commands to do just about anything you can do in Windows except it's more work, you can copy, move, del files, etc. To get out of DOS just type Exit at the command prompt. You need to find yourself a book on DOS commands to know how to work it.
Explain what D.O.S means
Disk operating System
Advantages of using a command-line driven U.I
Disadvantages of using a command-line driven U.I
- Commands must be typed correctly and in the right order or the command will not work
- An inexperienced user can sometimes find a command driven program difficult to use because of the number of commands that have to be learnt
Add of an image of a command line U.I
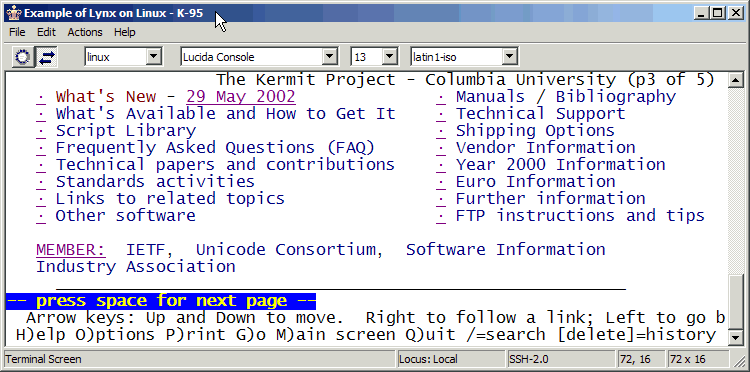
Explain how a menu U.I works
The user is offered a simple menu from which to choose an option. One menu often leads to a further menu. Part of the screen may have an instruction followed by a numbered list of options to choose from.
A menu bar is the set of options at the top of the screen. When an option is chosen a drop-down menu may be offered.
Features of menu driven interfaces include:
- They are easy to use as the user does not have to remember sets of commands.
- They are user friendly - you can often guess your way around the options.
- They can be irritating if there are too many levels of menus to move around - with a command-line interface you can go to the option required immediately.

List the advantages of a Menu driven U.I
List the disadvantages of a menu driven U.I
 - You often can't go to the exact place you want right at the start. You have to work your way through the menu screens even if you know where you want to get to.
- You often can't go to the exact place you want right at the start. You have to work your way through the menu screens even if you know where you want to get to.
- The menu can take up a large part of the screen so you have to keep flicking back and forwards between applications
- If the menu is poorly designed it might be hard to read e.g. writing is too small for people with poor sight, colours might clash and be difficult to read, font style might be hard to read.
Image of a menu driven U.I

Explain how a menu G.U.I works
There are other ways to move a pointer around including trackballs, buttons, touchpads, touchscreens, joysticks and video game controllers.
The computer will do different things depending upon where the pointer is on the screen and how a button is pressed. A program on the computer is constantly checking for the location of the pointer on the screen, any movement of the mouse, and any buttons pressed. It even checks to see how fast they are pressed. This program will decide what the user wanted to do by these actions and try to do it.
For example, if you move the pointer on the screen over the file menu and press a mouse button you will see a list appear. Moving the pointer down the list to print and clicking again will tell the computer that you want to print a paper copy of this page. It will respond by creating a new dialog box asking you how you want to have the page print out.
What does W.I.M.P stand for?
Window, Icon, Menu, Pointing Device
List the advantage of using a G.U.I
Advantages
- it can be user-friendly and speed up the user's work.
- it can be more attractive for non-technical people.
- in general, it looks more professional (but this does not mean it is always the best solution).
- it can be more attractive for non-technical people.
- in general, it looks more professional (but this does not mean it is always the best solution).
List the disadvantage of using a G.U.I
Disadvantages
- when it is not properly built, it can be very difficult to work with.
- it generally requires more memory resources than a non-graphical one.
- it might require the installation of additional software, e.g., the "runtime environment" in the case of java.
- depending on the programmer, it might require more time to be implemented
- when it is not properly built, it can be very difficult to work with.
- it generally requires more memory resources than a non-graphical one.
- it might require the installation of additional software, e.g., the "runtime environment" in the case of java.
- depending on the programmer, it might require more time to be implemented
Image of G.U.I

What key points should any designer of a U.I take into consideration when they are designing a new one?
1) Who your audience is? Physicists and Motorcycle lovers are different audiences. How technically saavy is your average user? Your interface should explain itself to the right users.
2) What exactly are you going to do? How easy it will be for a user to use your system as they desire? A form with 50 buttons on it is a little overwhelming. A web page with 20 modules on it is just noisy.
3) Will your application need to support more then 1 language?
4) How hard would it be to make your application a webpage, a gui form and a console application?
Keep your code for data and logic seperate from the UI.
2) What exactly are you going to do? How easy it will be for a user to use your system as they desire? A form with 50 buttons on it is a little overwhelming. A web page with 20 modules on it is just noisy.
3) Will your application need to support more then 1 language?
4) How hard would it be to make your application a webpage, a gui form and a console application?
Keep your code for data and logic seperate from the UI.
Sunday, 15 April 2012
ICT BLOGGER HOMEWORK EASTER
Networks
Networks can be made locally or gloabally. A local network is called a LAN which stands for Locan Area Network. A global network is called WAN which stands for Wide Area Network
There are three types of network connections. Ring Bus and Star
A Bus Network

Advantages
Disadvantage
Only one computer at a time can send a message; therefore, the number of computers attached to a bus network can significantly affect the speed of the network. A computer must wait until the bus is free before it can transmit.
A Star Network

Each computer on a star network communicates with a central hub that resends the message either to all the computers (in abroadcast star network) or only to the destination computer (in a switched star network). The hub in a broadcast star network can be active or passive.
An active hub regenerates the electrical signal and sends it to all the computers connected to it. This type of hub is often called amultiport repeater.
Advantages
A Ring Network

Every computer is connected to the next computer in the ring, and each retransmits what it receives from the previous computer. The messages flow around the ring in one direction. Since each computer retransmits what it receives, a ring is an active network and is not subject to the signal loss problems a bus experiences.
Advantages
Disadvantages
Generic Software
Generic software is software which many companies make an example of this is a word processor, a spread sheet sorftware and a powerpoint software.
Generic software include buttons and logos that can be easily recognised so that the use fo the button is clear even if the user has never used this specific software, an example of this would be the save icon as it is the same or very similar on all software.
Computer Misuse Act
Data stored electronically is easier to misuse; that software should not be copied without permission; the consequences of software piracy; that hacking can lead to corruption of data, either accidentally or on purpose.
Types of computer misuse
Misuse of computers and communications systems comes in several forms:Hacking
Hacking is where an unauthorised person uses a network, Internet or modem connection to gain access past security passwords or other security to see data stored on another computer. Hackers sometimes use software hacking tools and often target, for example, particular sites on the Internet.Data misuse and unauthorised transfer or copying
Copying and illegal transfer of data is very quick and easy using online computers and large storage devices such as hard disks, memory sticks and DVDs. Personal data, company research and written work, such as novels and textbooks, cannot be copied without the copyright holder's permission.Copying and distributing copyrighted software, music and film
This includes copying music and movies with computer equipment and distributing it on the Internet without the copyright holder's permission. This is a widespread misuse of both computers and the Internet that breaks copyright regulations.Email and chat room abuses
Internet services such as chat rooms and email have been the subject of many well-publicised cases of impersonation and deception where people who are online pretend to have a different identity. Chat rooms have been used to spread rumours about well known personalities. A growing area of abuse of the Internet is email spam, where millions of emails are sent to advertise both legal and illegal products and services.Pornography
A lot of indecent material and pornography is available through the Internet and can be stored in electronic form. There have been several cases of material, which is classified as illegal, or which shows illegal acts, being found stored on computers followed by prosecutions for possession of the material.Identity and financial abuses
This topic includes misuse of stolen or fictional credit card numbers to obtain goods or services on the Internet, and use of computers in financial frauds. These can range from complex well thought out deceptions to simple uses such as printing counterfeit money with colour printers.Viruses
Viruses are relatively simple programs written by people and designed to cause nuisance or damage to computers or their files.The Computer Misuse Act (1990)
This was passed by Parliament and made three new offences:- Accessing computer material without permission, eg looking at someone else's files.
- Accessing computer material without permission with intent to commit further criminal offences, eg hacking into the bank's computer and wanting to increase the amount in your account.
- Altering computer data without permission, eg writing a virus to destroy someone else's data, or actually changing the money in an account.
The Data Protection Act
This was introduced to regulate personal data. This helps to provide protection against the abuse of personal information. Find out more about the Data Protection Act.
Copyright
Copyright law
This provides protection to the owners of the copyright and covers the copying of written, musical, or film works using computers. FAST is the industry body which is against software theft. You can find out more about it in the Copyright section.There have been cases where laws such as Copyright have been used to crack down on file sharing websites or individuals who store and illegally distribute copyrighted material, eg music. There is a massive problem with many people around the world obtaining copyrighted material illegally.
Weblogs + Social Networks
What is social networking?
Social networking sites, while they include the ability to post written material to the web like blogs do, revolve much more around the ability of an individual to build a web "presence" and to create visible links with others in the network. What writing there is on a social networking site is often in computer slang, intended to be "different." These sites often allow the ability to place music, photo, and video content on the site, allowing the individual to showcase their likes and dislikes. A form of text messaging is often included as well, with a history of the messages appearing on the site. Again, all of the features of social networking sites are intended to create social interactions with others.
Subscribe to:
Comments (Atom)